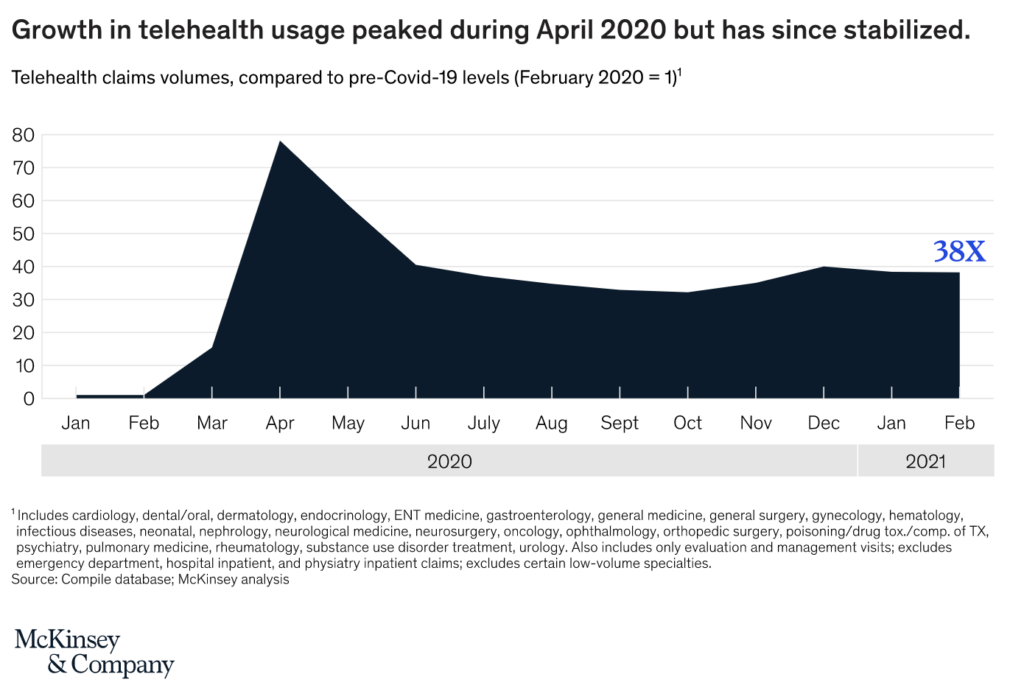
Recent reports estimate a five-fold increase in virtual consultations, reaching a total of 400 million visits and about $25bn in value. Some parts of the US saw an increase in telehealth usage from 1% to 85%. While this spike in usage has stabilized, telehealth consultations have increased 38 times compared to pre-COVID levels.
In non-emergency conditions, HIPAA requirements around telehealth are quite strict. However, to cope with the drastic increase in telehealth consultations, the HHS relaxed these regulations to provide temporary relief in response to the COVID-19 pandemic. This allowed generic, non-public video communications such as Apple FaceTime, Facebook Messenger video chat, Google Hangouts video, Zoom, or Skype to be used without the risk that the Office of Civil Rights (OCR) will seek a penalty for HIPAA.
The HHS can tighten the regulations again at their discretion. So it is critical for healthcare providers to ensure fully HIPAA compliant telehealth services to protect PIH and prevent non-compliance penalties.
What does HIPAA compliance entail?
For a telehealth platform to be HIPAA compliant, it must adhere to three rules:
- Privacy Rule – a healthcare provider must either obtain authorization from a patient that their data can be shared, or the healthcare provider must enter a business associate contract with the communications service provider.
- Security Rule – providers must have controls in place to prevent any unauthorized access to or modification of PHI during its electronic transmission
- Breach Notification Rule – health care providers and businesses associate must notify any affected patients within 60 calendar days after discovering a breach of PHI
For a fully compliant telehealth application, both the healthcare provider and any third-party vendors such as technology suppliers must fulfill all three rules.
Below we will discuss how to develop a telehealth application that can handle PHI in a HIPAA compliant way with reference to each described rule.
What telehealth services must be HIPAA compliant?
The Congressional Research Service has defined four common telehealth modalities:
- Clinical video health or live-feed video – this allows a healthcare provider to view, diagnose, monitor, and treat medical conditions of the patient in real-time via live video;
- Mobile health – allows providers to deliver educational materials and other healthcare resources through a patient’s mobile application;
- Remote patient monitoring – enables providers to carry out daily case management services for the patients with chronic medical conditions; and
- Store-and-forward technology – a provider uses a health information technology system to exchange information related to a patient’s medical record.
Every telehealth platform that supports one or more of these modalities must adhere to the three rules described above to achieve HIPAA compliance.
Privacy rule
The Privacy Rule looks at the parties that are authorized to access a patient’s health information. HIPAA describes two ways in which this can be accomplished. The first, easier way, requires the patient to offer their consent that their data can be shared with the technology providers involved in delivering the telehealth application
The second, a more adequate and scalable way of adhering to the Privacy Rule, is that the technology vendor will enter a business associate agreement with the healthcare provider. Failure to enter into a HIPAA-compliant business associate agreement with all vendors that are provided with or given access to PHI is one of the most common HIPAA violations.
The HIPAA Privacy Rule gives patients the right to access their medical records and obtain copies on request. This allows patients to check their records for errors and share them with other entities and individuals. Denying patients copies of their health records, overcharging for copies, or failing to provide those records within 30 days is a violation of HIPAA. OCR made HIPAA Right of Access violations one of its key enforcement objectives in late 2019.
The HSS describes a business associate as a third party who provides certain services to healthcare providers as described in a business associate agreement.. They can also be a subcontractor that creates, receives, maintains, or transmits protected health information on behalf of another business associate. The HIPAA rules require that all entities included in business associate agreements will appropriately safeguard protected health information.
A valid business associate agreement, as any contract, must clearly define the terms of the contract between the healthcare provider and third party. The agreement must also define processes for dealing with data breaches and handling audits from the Office of Civil Rights.
Security rule
The Security Rule requires covered entities to maintain administrative, physical, and technical safeguards to prevent threats or hazards to the security of electronic PHI. The technical safeguards must include transmission security to protect against unauthorized access to electronic health information.
These measures must have integrity controls to ensure the electronically transmitted PHI is not improperly modified until disposed of, and mechanisms to encrypt electronically protected health information whenever deemed appropriate.
To comply with the security rule, telehealth applications should contain the following security functions:
- User management and Access control
-
- Emergency access procedures – these functionalities provide medical staff with rights and/or privileges to access and perform functions when necessary for a business to operate under emergency conditions.
- Automatic logoff – Imposing time-out limits for users to prevent them staying logged in accidentally
- User authentication – all authentication processes must take place over HTTPS. We also recommend implementing additional security mechanisms for both patient and staff authentication. You can implement multi-factor authentication by either using a mobile telephone number, a trusted device, or even biometrics such as face ID or fingerprint scanners.
- End-to-end encryption – application-layer encryption of PHI data with a minimum 128-bit level of encryption, such as AES 128
- Audit controls – maintaining logs of actions and changes to ensure full traceability. These need to include timestamps and digital signatures, covering everything from document changes and detail updates to external communications and printing requests.
- Data Integrity – this refers to the accuracy and consistency of data over its lifecycle. Each time data is replicated or transferred, it should remain intact and unaltered between updates. Error checking methods and validation procedures are typically relied on to ensure the integrity of data that is transferred or reproduced without the intention of alteration
- Transmission security – any communication of PHI must be done via secure channels, and communication via consumer platforms such as personal email accounts violates HIPAA compliance. Further, any emailing of ePHI to a personal email account could be considered theft, the repercussions of which could be far more severe than termination of an employment contract.
- Risk Assessment – telemedicine applications need to undergo a risk assessment process, which should cover seven telemedicine security threat areas:
- User or Patient
- Telemedicine Device
- Home Network
- Gateway device
- Internet (public network)
- Telemedicine system
- Medical team
- Secure Connection – an additional security factor to consider for high-privilege users such as health practitioners and administrators is accessing the platform through an authorized virtual private network. This will decrease the risk of malicious actors accessing the system without access to the healthcare provider’s private corporate network.
Breach notification rule
Under the Breach Notification Rule, healthcare providers must notify affected individuals within 60 calendar days in case of a breach of unsecured PHI. They must also notify the Secretary of HHS, and, for certain large breaches, the media. Unsecured PHI refers to data that can be directly accessed by malicious actors, such as non-encrypted data.
To meet the Breach Notification Rule requirements, telehealth applications need the following capabilities:
- Data Encryption – if data is encrypted at the minimum level specified by HIPAA, the information is rendered useless for any malicious actors. Any breach of encrypted data does not need to be reported under this rule
- Breach Detection – most data breaches take place through compromised accounts that share PIH data onto external platforms. User and Entity Behavior Analytics (UEBA) platforms monitor and highlight suspicious behavior for further investigation
- Alerts and incidents – upon identifying data breaches, alerts and incidents can be used to inform relevant compliance and security analysts, as well as monitor and manage the event.
Automatic notifications – to support compliance with the breach notification rule, the telehealth application may contain a function that automatically notifies affected users of the breach via an approved communication channel.
Qubika for healthcare
Qubika is a software development company that is currently working on the next healthcare platforms for organizations that are paving the way in the industry. We have helped numerous healthcare providers develop and maintain HIPAA-compliant health and telehealth applications.
We leverage our expertise in telehealth development to bake in HIPAA compliance functionalities in the applications we develop, such that our solutions adhere to all rules from day one. To learn more about our services enter healthcare software development company.