How we increase the cybersecurity of our customers’ platforms, CI/CD workflows and applications
Learn about how our Cloud, SRE & Cybersecurity team utilize some best practices to enhance cybersecurity in our client’s products.

Financial services
Expertise in core banking, BaaS integrations, payments, and GenAI-enhanced financial solutions.

Healthcare
People-centric healthcare design and solutions, from virtual care, integrations, to smart devices.

Insurance
Modern solutions including self-service, on-demand, and algorithm-driven personalization.

We’re purposefully shaping the digital future across a range of industries.
Discover some of our specific industry services.
Discover moreAugust 2, 2021
Recent reports indicate a significant increase in virtual consultations, with telehealth consultations increasing 38 times compared to pre-COVID levels. To ensure HIPAA compliance in telehealth services, healthcare providers must adhere to certain rules. Continue reading to learn more!

Recent reports estimate a five-fold increase in virtual consultations, reaching a total of 400 million visits and about $25bn in value. Some parts of the US saw an increase in telehealth usage from 1% to 85%. While this spike in usage has stabilized, telehealth consultations have increased 38 times compared to pre-COVID levels.
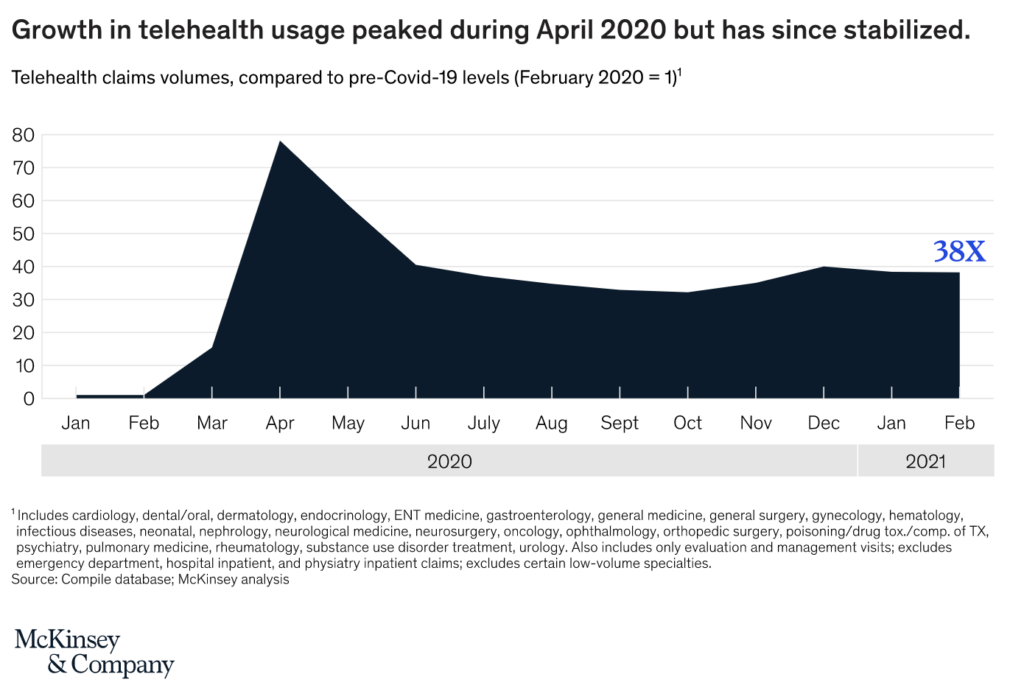
In non-emergency conditions, HIPAA requirements around telehealth are quite strict. However, to cope with the drastic increase in telehealth consultations, the HHS relaxed these regulations to provide temporary relief in response to the COVID-19 pandemic. This allowed generic, non-public video communications such as Apple FaceTime, Facebook Messenger video chat, Google Hangouts video, Zoom, or Skype to be used without the risk that the Office of Civil Rights (OCR) will seek a penalty for HIPAA.
The HHS can tighten the regulations again at their discretion. So it is critical for healthcare providers to ensure fully HIPAA compliant telehealth services to protect PIH and prevent non-compliance penalties.
For a telehealth platform to be HIPAA compliant, it must adhere to three rules:
For a fully compliant telehealth application, both the healthcare provider and any third-party vendors such as technology suppliers must fulfill all three rules.
Below we will discuss how to develop a telehealth application that can handle PHI in a HIPAA compliant way with reference to each described rule.
The Congressional Research Service has defined four common telehealth modalities:
Every telehealth platform that supports one or more of these modalities must adhere to the three rules described above to achieve HIPAA compliance.
The Privacy Rule looks at the parties that are authorized to access a patient’s health information. HIPAA describes two ways in which this can be accomplished. The first, easier way, requires the patient to offer their consent that their data can be shared with the technology providers involved in delivering the telehealth application
The second, a more adequate and scalable way of adhering to the Privacy Rule, is that the technology vendor will enter a business associate agreement with the healthcare provider. Failure to enter into a HIPAA-compliant business associate agreement with all vendors that are provided with or given access to PHI is one of the most common HIPAA violations.
The HIPAA Privacy Rule gives patients the right to access their medical records and obtain copies on request. This allows patients to check their records for errors and share them with other entities and individuals. Denying patients copies of their health records, overcharging for copies, or failing to provide those records within 30 days is a violation of HIPAA. OCR made HIPAA Right of Access violations one of its key enforcement objectives in late 2019.
The HSS describes a business associate as a third party who provides certain services to healthcare providers as described in a business associate agreement.. They can also be a subcontractor that creates, receives, maintains, or transmits protected health information on behalf of another business associate. The HIPAA rules require that all entities included in business associate agreements will appropriately safeguard protected health information.
A valid business associate agreement, as any contract, must clearly define the terms of the contract between the healthcare provider and third party. The agreement must also define processes for dealing with data breaches and handling audits from the Office of Civil Rights.
The Security Rule requires covered entities to maintain administrative, physical, and technical safeguards to prevent threats or hazards to the security of electronic PHI. The technical safeguards must include transmission security to protect against unauthorized access to electronic health information.
These measures must have integrity controls to ensure the electronically transmitted PHI is not improperly modified until disposed of, and mechanisms to encrypt electronically protected health information whenever deemed appropriate.
To comply with the security rule, telehealth applications should contain the following security functions:
Under the Breach Notification Rule, healthcare providers must notify affected individuals within 60 calendar days in case of a breach of unsecured PHI. They must also notify the Secretary of HHS, and, for certain large breaches, the media. Unsecured PHI refers to data that can be directly accessed by malicious actors, such as non-encrypted data.
To meet the Breach Notification Rule requirements, telehealth applications need the following capabilities:
Automatic notifications – to support compliance with the breach notification rule, the telehealth application may contain a function that automatically notifies affected users of the breach via an approved communication channel.
Qubika is a software development company that is currently working on the next healthcare platforms for organizations that are paving the way in the industry. We have helped numerous healthcare providers develop and maintain HIPAA-compliant health and telehealth applications.
We leverage our expertise in telehealth development to bake in HIPAA compliance functionalities in the applications we develop, such that our solutions adhere to all rules from day one. To learn more about our services enter healthcare software development company.

By Carin Carlin
Communication Specialist
Receive regular updates about our latest work
Learn about how our Cloud, SRE & Cybersecurity team utilize some best practices to enhance cybersecurity in our client’s products.

Check out this interview with Christian Cervero, BCP Bolivia’s head of alternative channels and digital solutions, to discover more about how they have achieved this success and their relationship with Qubika.
Check out this article from Ariel, Qubika’s CEO, about how telehealth applications are reshaping the US health ecosystem.

Receive regular updates about our latest work
Get in touch with our experts to review your idea or product, and discuss options for the best approach
Get in touch