It is neither new nor news that private and public companies face permanent, high exposure to cyber-attacks in multiple ways. Every quarter there is at least one major security breach in large companies across different industries. For example, Uber in 2022 suffered a security incident caused by a sequence of basic security bad practices. Medibank didn’t cover key aspects in the allocation of permissions. The consequence? Losses of money, time and reputation.
So even companies with very significant resources and budgets, still struggle with their cybersecurity. By not adopting rigorous security practices/controls, and not having a strong security culture throughout their organization, a security breach is often simply a matter of time.
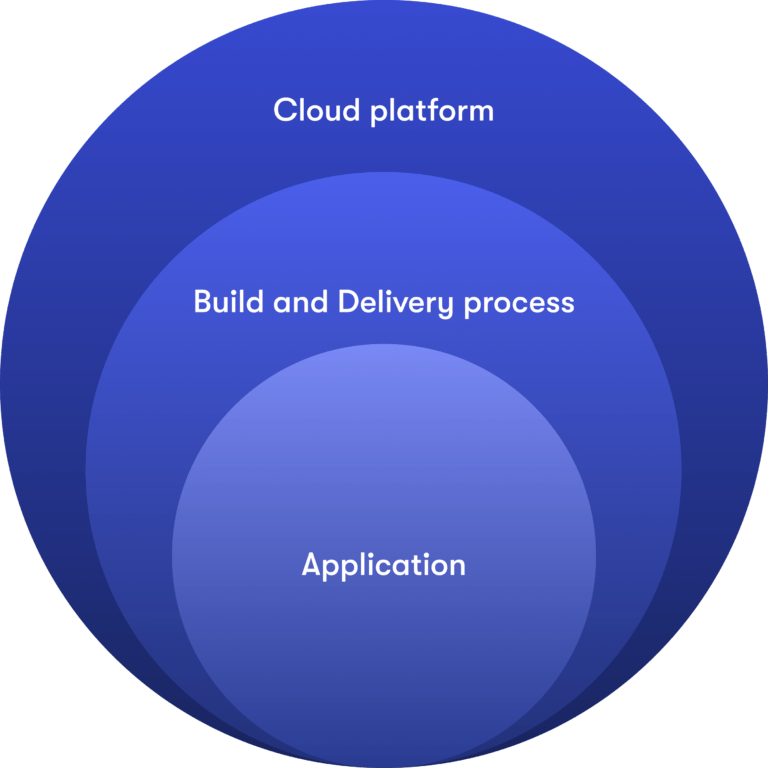
Here at Qubika, we’ve built out a portfolio of cybersecurity offerings, to help increase the security posture of our clients. We’ve structured the portfolio to match the typical components of a technology-based business.
The platform. Usually a businesses’ platform is a mix of a cloud provider (AWS/Azure/GCP), multiple Kubernetes clusters, containers or multiple virtual machines and is where the organization hosts their offered services and apps.
Software build and delivery processes. This refers to the software development process, the use of code versioning platforms such as GitHub/GitLab, and delivery pipelines of the app on the platform.
Application/code. This is the business logic written in a set of languages, scripts, designs, architectures, among others.
We perform a set of security assessments once we have identified the core elements of a client’s business, operations, and technology. From these evaluations, we construct a tailored security plan that prioritizes and addresses the most critical elements.
Our cybersecurity practice provides 5 main security assessments
- Cloud security assessment. This is a test that determines the attack surface in order to detect the impact of a successful attack on your platform.
- Kubernetes security assessment. This test determines the security posture of the cluster and the components that serve the application in order to identify the impact of a real attack on your services.
- Application security assessment. This test seeks to identify potential vulnerabilities in the application code before they reach a production environment (not a penetration test) and can be exploited by an attacker.
- CI/CD security assessment. This assessment seeks to identify vulnerabilities in the process of building the software as well as the process of delivering the resulting artifact to production. Generally the security analysis is done on CI/CD tools such as pipelines, repos, registries and Docker artifacts.
- Penetration testing. This assessment seeks to assess the security posture of a system, network, web application, mobile application or organization by simulating real-world attacks. The goal is to identify vulnerabilities in the target system or network before malicious attackers exploit them without affecting services in production.
The value of Qubika’s cybersecurity practice
Our cybersecurity practice helps organizations ensure business continuity by protecting critical information assets from cyber threats. To do this we align our efforts with the most prominent security frameworks in the market, coupled with the extensive experience of our certified experts in major brands, technologies, and topics including cloud, Kubernetes, application code and CI/CD security.
Our cybersecurity practice plays a critical role in adding value to our clients. By implementing robust security measures, we ensure that sensitive data remains protected from unauthorized access, theft, and cyber-attacks. We help to prevent potential financial losses resulting from security breaches, reputational damage, and legal liabilities.
Schedule a consultation
If your business requires an understanding of your cloud platform’s security posture, best security practices for your Kubernetes cluster, or appropriate security controls for your application code, look no further. Contact us today.